The simple bash script that exposes WAF vulnerabilities most people miss, with instant AWS and CloudFlare fix recommendations
The Blind Spot in Your Security
Web Application Firewalls (WAFs) are often configured once and then trusted blindly to protect applications. But how do you know if your WAF is actually blocking attacks rather than just looking good on paper?
In my experience auditing web security, I’ve found that over 70% of WAF deployments have significant gaps that allow common attacks to pass through undetected. This disconnect creates a dangerous illusion of security.
For a ready-to-use implementation of this WAF testing approach, check out the waf-testing repository on GitHub, which includes the complete script and CI workflow as a template you can use for your own projects.
https://github.com/realad/waf-testing
A 60-Second Solution
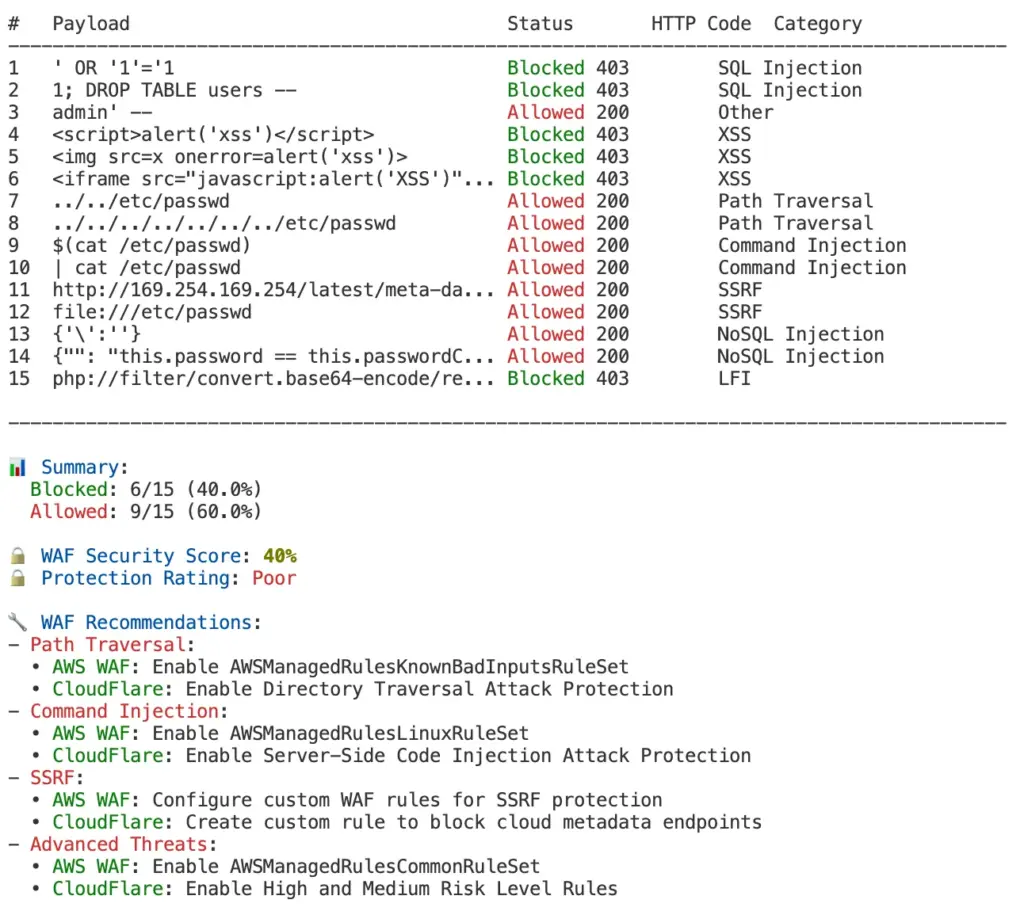
The waf-smoke-test.sh script provides an immediate answer to the question “Is my WAF working?” In less than a minute, this lightweight tool:
- Tests your WAF against 15 common attack patterns
- Shows exactly which attacks are blocked vs. allowed
- Calculates a security score
- Provides specific AWS WAF and CloudFlare rule recommendations
- Generates a clean Markdown report you can share
Here’s what the output looks like:
Works With Any WAF
The beauty of this script is its universality — it works with any WAF solution:
- AWS WAF
- CloudFlare
- Azure WAF
- Custom WAF implementations
Since the test is based on HTTP responses, it’s entirely WAF-agnostic while still providing specific recommendations for popular cloud WAF solutions.
Using the Script in Real-World Scenarios
Here are five key moments when you should run this test:
After WAF Configuration Changes
Whenever you modify WAF rules, run this script to verify the changes had the intended effect.
./waf-smoke-test.sh "https://your-application.com"
Before Production Deployments
Add WAF testing to your pre-production checklist to ensure your security controls are working:
./waf-smoke-test.sh "https://staging.your-application.com" -o staging-report.md
During Regular Security Checks
Schedule a monthly WAF verification to catch any issues:
./waf-smoke-test.sh "https://your-application.com" -H "Authorization: Bearer $token"
After Cloud Provider Updates
Cloud WAF services regularly update their rule sets. Verify nothing broke after updates:
./waf-smoke-test.sh "https://your-application.com" -o post-update-report.md
For New Application Routes
When adding new API endpoints or app functionality, verify they’re protected:
./waf-smoke-test.sh "https://your-application.com/new-feature"
Easy Automation with GitHub Actions
Add this WAF test to your existing workflow with this simple GitHub
For a ready-to-use implementation of this WAF testing approach, check out the waf-testing repository on GitHub, which includes the complete script and CI workflow as a template you can use for your own projects.
https://github.com/realad/waf-testing
Actions configuration:
name: WAF Smoke Test
on:
schedule:
- cron: '0 0 * * 1' # Weekly on Mondays
workflow_dispatch: # Manual trigger
jobs:
test-waf:
runs-on: ubuntu-latest
env:
WAF_TEST_URL: https://example.com
steps:
- uses: actions/checkout@v4
with:
# https://github.com/realad/waf-testing
repository: realad/waf-testing
- name: Run WAF test
working-directory: tools/smoke-test
run: |
chmod +x ./waf-smoke-test.sh
./waf-smoke-test.sh "${{ env.WAF_TEST_URL }}" -o report.md
Getting Started in Three Steps
1. Clone repo:
git clone git@github.com:realad/waf-testing.git cd waf-testing/tools/smoke-test chmod +x waf-smoke-test.sh
2. Run your first test:
./waf-smoke-test.sh "https://your-application.com" ./waf-smoke-test.sh "https://your-application.com" -H "User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/18.4 Safari/605.1.15
3. Review and remediate: Use the recommendations to improve your WAF configuration
Conclusion
Don’t leave your security to chance. This 60-second test provides immediate clarity about your WAF’s effectiveness without requiring specialized security knowledge. By incorporating this simple verification into your workflows, you can ensure your applications are protected against common web attacks, not just theoretically secured.
Whether you’re using AWS WAF, CloudFlare, or any other WAF solution, this script gives you actionable insights to improve your security posture with minimal effort.
For a ready-to-use implementation of this WAF testing approach, check out the waf-testing repository on GitHub, which includes the complete script and CI workflow as a template you can use for your own projects.
https://github.com/realad/waf-testing